These are some of the network captures that I did using wireshark, when Conficker infected my machine. I had a hard time removing it. But in the beginning I didnt even know if something is wrong. I did some network forensic kind of thing just to ensure that some weird and unexplained network traffic was going on. :( . Now I am presenting them as facts and questions that came to my mind. Sometimes when you dont know if your computer is compromised by a worm or trojan, these kind of symptoms are the ones you can look out for. Wireshark is an excellent open source tool for monitoring the network traffic coming in and out of your system.
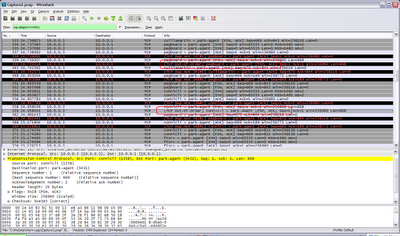 Fact #1: Use of p2p: the PSH flag set in TCP packets.
Fact #1: Use of p2p: the PSH flag set in TCP packets.
Q: p2p?? I aint using any p2p software, what the hell? why these PSH flags are set?
In general the TCP packets used by p2p (peer to peer) protocol have PSH (PUSH) flag set. Whenever you see PSH flag set in TCP packets. You can be almost sure of p2p in action. p2p is not a common protocol, it comes into picture only if you are using p2p softwares like Kaza lite etc. Otherwise it sure could be a cause of worry. The PSH flag set implies that the TCP packets are intended to be "push" across the buffers ahead of any other data. For this reason p2p traffic is notorious for eating up bandwidth and is generally banned in corporate networks. Also p2p isnt a very reliable means of obtaining things. You never know the benign executable (that came in disguise of your favorite game) could be a trojan or a bot. One click and your computer becomes the zombia of a botnet.
 Fact #2: Whenever I connect to the network, my machine starts asking for MAC addresses of all possible hosts on my LAN.
Fact #2: Whenever I connect to the network, my machine starts asking for MAC addresses of all possible hosts on my LAN.
Q: Why would anyone do that? There is something, and this is a common sign of a worm which is trying to scan the entire LAN for vulnerable hosts.
This is a sureshot sign of trouble. If your computer is searching the whole subnet (say 10.0.0,1 to 10.0.0.254), its trying to figure out who else is present on your LAN. If any host replies back, the worm will try to infect it. The netbios (port 135, 139, 445) services of a windows machine are available to the LAN only. Any worm outside the LAN cannot attack it. But if any machine in your LAN is infected, chances are that all vulnerable windows machines will get infected. Unless your antivirus and OS is updated to face the most recent vulnerabilities.
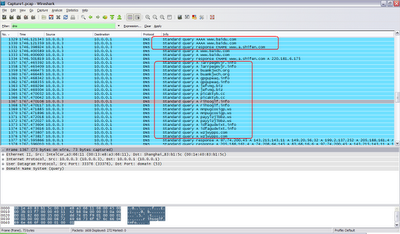
Fact #3: My machine trying to access unknown websites?? Oh, atleast they are unknown to me.
Q: why?? may be trying to get updates for the 'thing'?
Conficker uses an algorithm for calculating the rate of infection. If the rate is too fast, it would eat up the network bandwidth which may attract unwanted attention of network admins. If the rate is too slow, well conficker surely doesnt want this. Conficker tries to communicate some popular websites to find out the round-trip time and based on the results it tries to create a rate of infection that matches with internet speed of the victim host computer. I got this reasoning from the internet, possibly an antivirus site.
In other cases the worm might be trying to get updates for itself from hacking or compromised sites. The worm might be downloading the next instruction set, or even more powerful malware, adware etc.
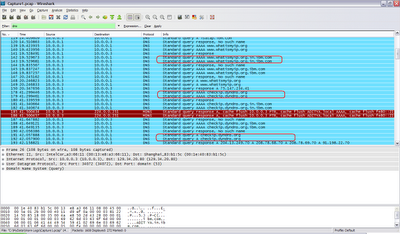
Fact #4: Trying to get my IP address. :(
Q: This could be a trojan or a bot.
By finding and sending my IP address, a bad guy/cracker can try to gain remote access to my computer. Well I dont really think so, I aint that special. I am just another bot in the bot herder's army.
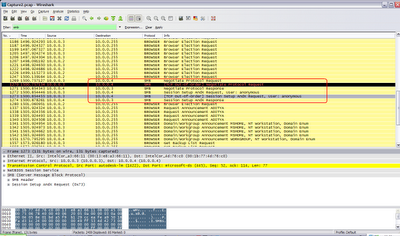
Fact #5:SMB negotiation, trying to gain anonymous access through port 445.
Q: Now I am sure this thing has something to do with a microsoft smb vulnerability, or may be its just trying something with anonymous shares.
Well, microsoft has its share of security problems. Whenever a remotely exploitable vulnerability appears, you can always expect a new worm coming in. No surprises here. This makes business happen, antiviruses get their acknowledgment. Advisories are out. And the bad guys make money too. Windows security gets another blow. And a lot of people lose money as well.
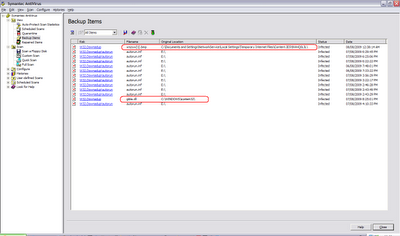
Fact #6: This was the last part, the hidden dll was in the form of a bmp image file hidden deep inside the caves of Internet Explorer.
Q: Why couldnt I find it myself?? huh!
Catching a popular worm without an antivirus is very hard these days. Although in my past I cleaned some of the relatively 'friendly' worms without using an antivirus at all. yeah they would let me sneak in ultimately give up their positions. Its fun and its like solving a puzzle.
Q: p2p?? I aint using any p2p software, what the hell? why these PSH flags are set?
In general the TCP packets used by p2p (peer to peer) protocol have PSH (PUSH) flag set. Whenever you see PSH flag set in TCP packets. You can be almost sure of p2p in action. p2p is not a common protocol, it comes into picture only if you are using p2p softwares like Kaza lite etc. Otherwise it sure could be a cause of worry. The PSH flag set implies that the TCP packets are intended to be "push" across the buffers ahead of any other data. For this reason p2p traffic is notorious for eating up bandwidth and is generally banned in corporate networks. Also p2p isnt a very reliable means of obtaining things. You never know the benign executable (that came in disguise of your favorite game) could be a trojan or a bot. One click and your computer becomes the zombia of a botnet.
Q: Why would anyone do that? There is something, and this is a common sign of a worm which is trying to scan the entire LAN for vulnerable hosts.
This is a sureshot sign of trouble. If your computer is searching the whole subnet (say 10.0.0,1 to 10.0.0.254), its trying to figure out who else is present on your LAN. If any host replies back, the worm will try to infect it. The netbios (port 135, 139, 445) services of a windows machine are available to the LAN only. Any worm outside the LAN cannot attack it. But if any machine in your LAN is infected, chances are that all vulnerable windows machines will get infected. Unless your antivirus and OS is updated to face the most recent vulnerabilities.
Fact #3: My machine trying to access unknown websites?? Oh, atleast they are unknown to me.
Q: why?? may be trying to get updates for the 'thing'?
Conficker uses an algorithm for calculating the rate of infection. If the rate is too fast, it would eat up the network bandwidth which may attract unwanted attention of network admins. If the rate is too slow, well conficker surely doesnt want this. Conficker tries to communicate some popular websites to find out the round-trip time and based on the results it tries to create a rate of infection that matches with internet speed of the victim host computer. I got this reasoning from the internet, possibly an antivirus site.
In other cases the worm might be trying to get updates for itself from hacking or compromised sites. The worm might be downloading the next instruction set, or even more powerful malware, adware etc.
Fact #4: Trying to get my IP address. :(
Q: This could be a trojan or a bot.
By finding and sending my IP address, a bad guy/cracker can try to gain remote access to my computer. Well I dont really think so, I aint that special. I am just another bot in the bot herder's army.
Fact #5:SMB negotiation, trying to gain anonymous access through port 445.
Q: Now I am sure this thing has something to do with a microsoft smb vulnerability, or may be its just trying something with anonymous shares.
Well, microsoft has its share of security problems. Whenever a remotely exploitable vulnerability appears, you can always expect a new worm coming in. No surprises here. This makes business happen, antiviruses get their acknowledgment. Advisories are out. And the bad guys make money too. Windows security gets another blow. And a lot of people lose money as well.
Fact #6: This was the last part, the hidden dll was in the form of a bmp image file hidden deep inside the caves of Internet Explorer.
Q: Why couldnt I find it myself?? huh!
Catching a popular worm without an antivirus is very hard these days. Although in my past I cleaned some of the relatively 'friendly' worms without using an antivirus at all. yeah they would let me sneak in ultimately give up their positions. Its fun and its like solving a puzzle.
